Not so long time ago, I submitted my presentation proposal on CONFidence’s Call For Papers. CONFidence is one of the best European IT Sec conferences that I love to attend due to very good presentations quality and hackish^H^H atmosphere ;-)
This year I decided to actively attend as a speaker with my presentation about pentesting iOS apps using jailed iDevice. I sent my proposal, and when I received the approval, I visited the conference’s website in order to check if I’m included in the speakers list for sure (in SecuRing it’s common to prank your colleagues like for instance sending emails from the fake server, haha).
I entered the website and found myself, yay!
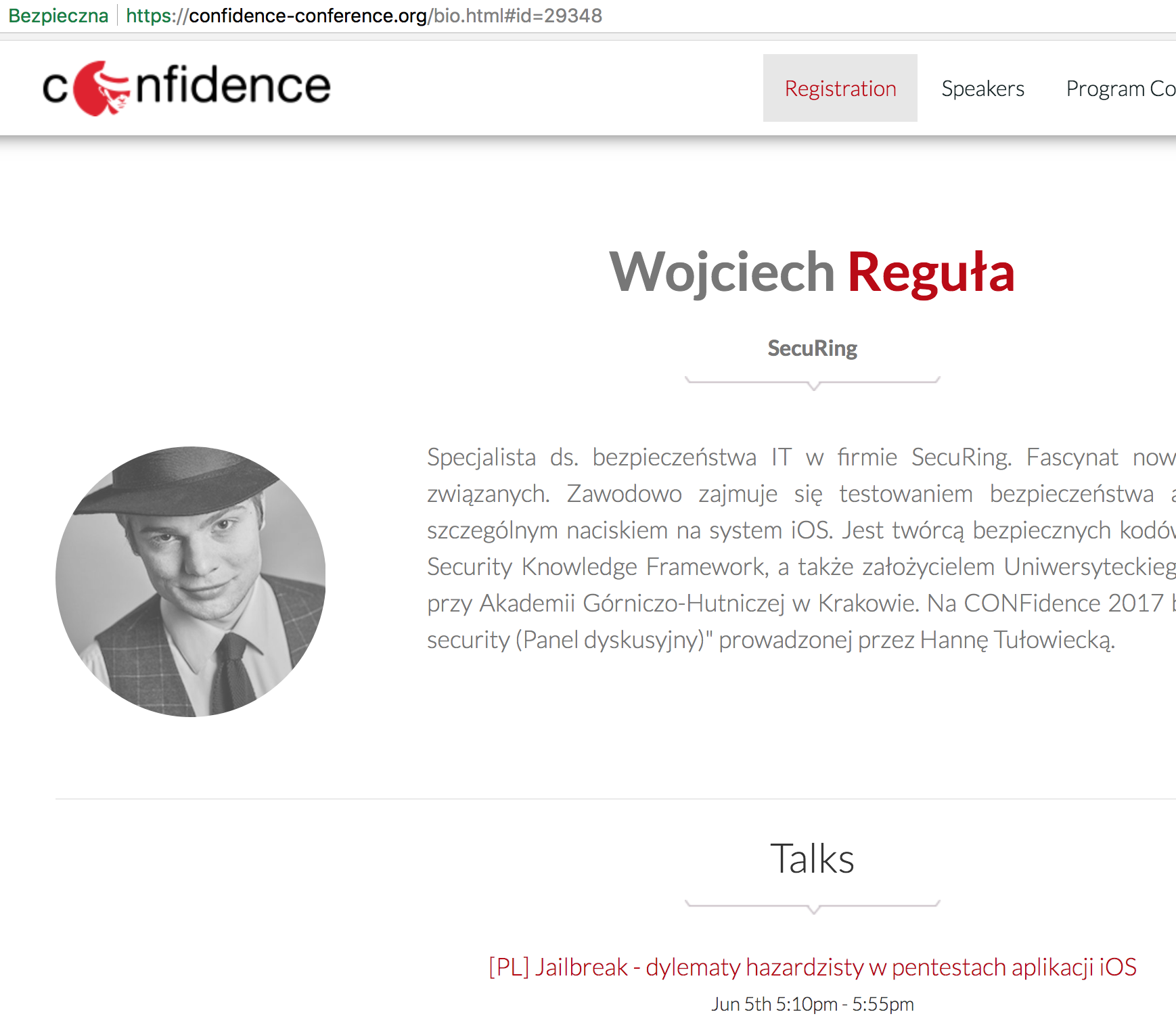
If you are interested in the IT Sec field, a numeric parameter in the URL probably triggers something in your brain. I have opened Chrome’s dev tools immediately and seen XHR request to https://eventory.cc.
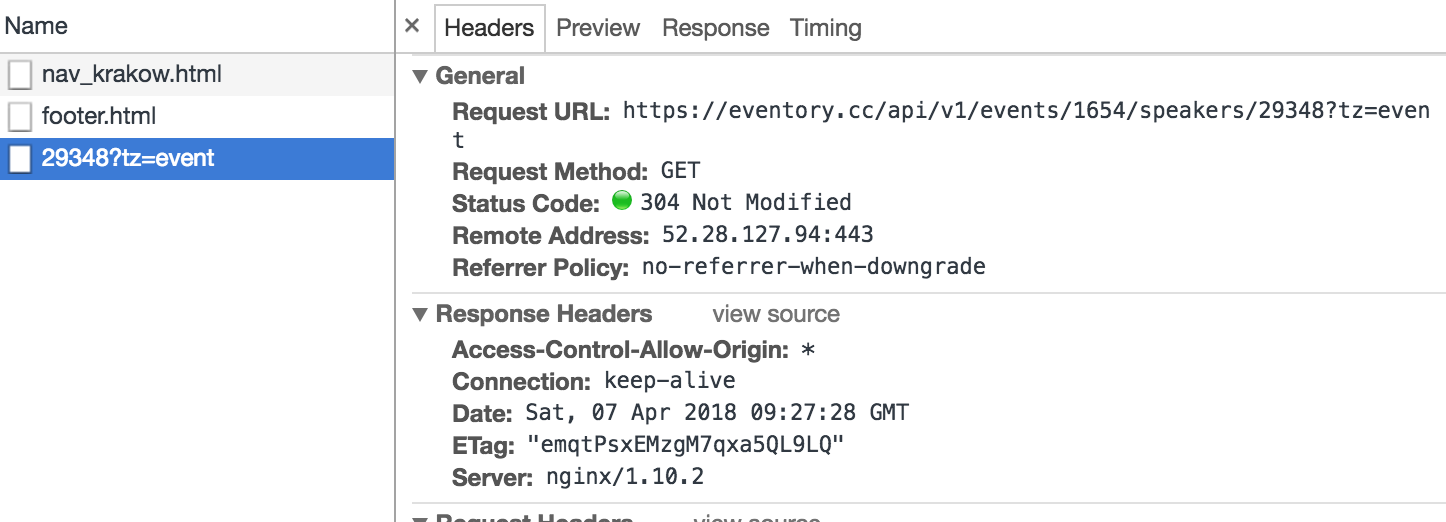
Hmm, the ID from XHR’s ‘Request URL’ is the same that we saw earlier. Wouldn’t it be fun if we can perform little path traversal and reflectively load our speaker?
I have registered in Eventory, created a fake conference, and made Bob The Builder the main speaker.
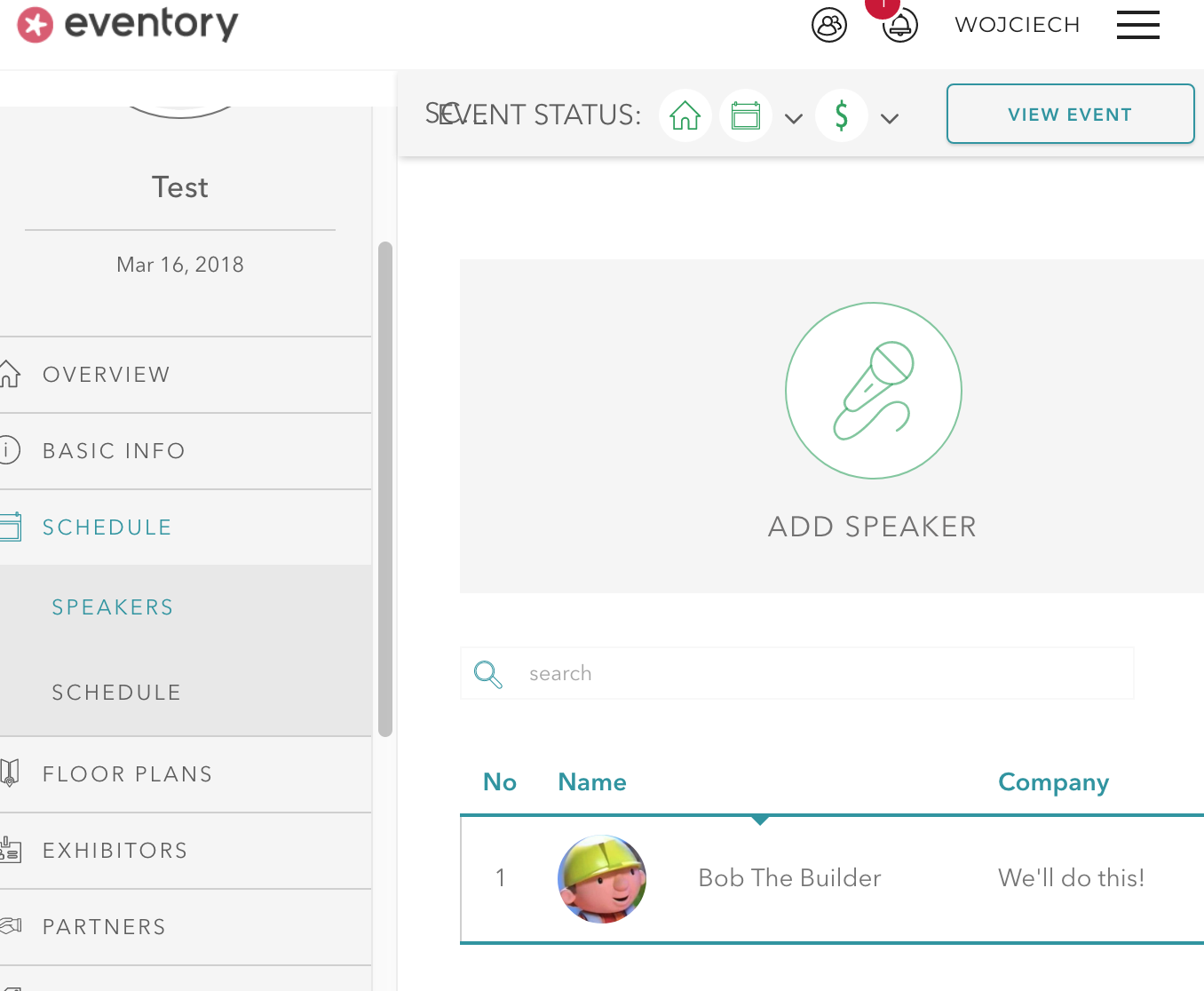
Next step was to change the URL from
https://confidence.org.pl/bio.html#id=29348
to
https://confidence.org.pl/bio.html#id=../../1883/speakers/29393
The result was, of course:
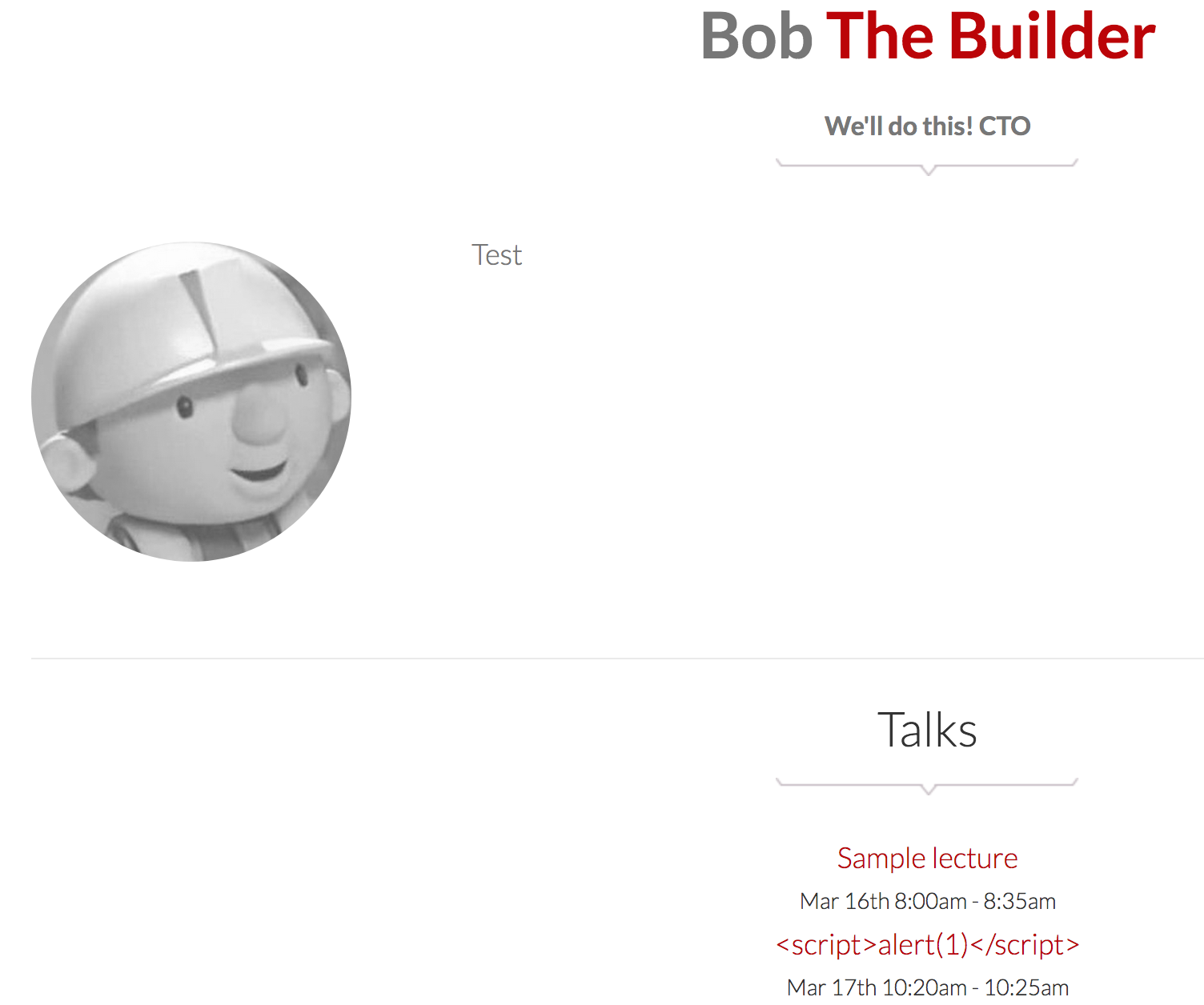
Voilà! CTO Bob the Builder included. As you can see in the talks section, the description is carefully encoded, so it there was no XSS vulnerability. It makes this post title rather clickbait since it’s hard to say now that this path traversal is a serious vulnerability.
##The revenge
This ‘issue’ was reported to the CONFidence, they have fixed this and the topic was closed… up to April Fools’ Day! When I woke up, I saw tons of messages like ‘LOL, check CONFidence’s fanpage!’. And I did, haha.
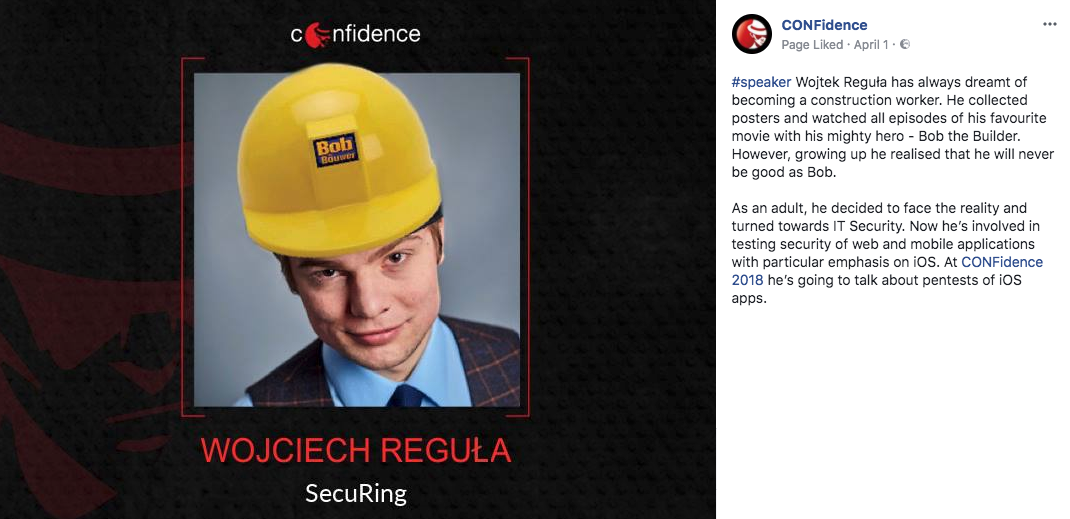
If you have seen this post and you have been thinking like ‘funny, but why Bob The Builder?’ here is the answer ;-).